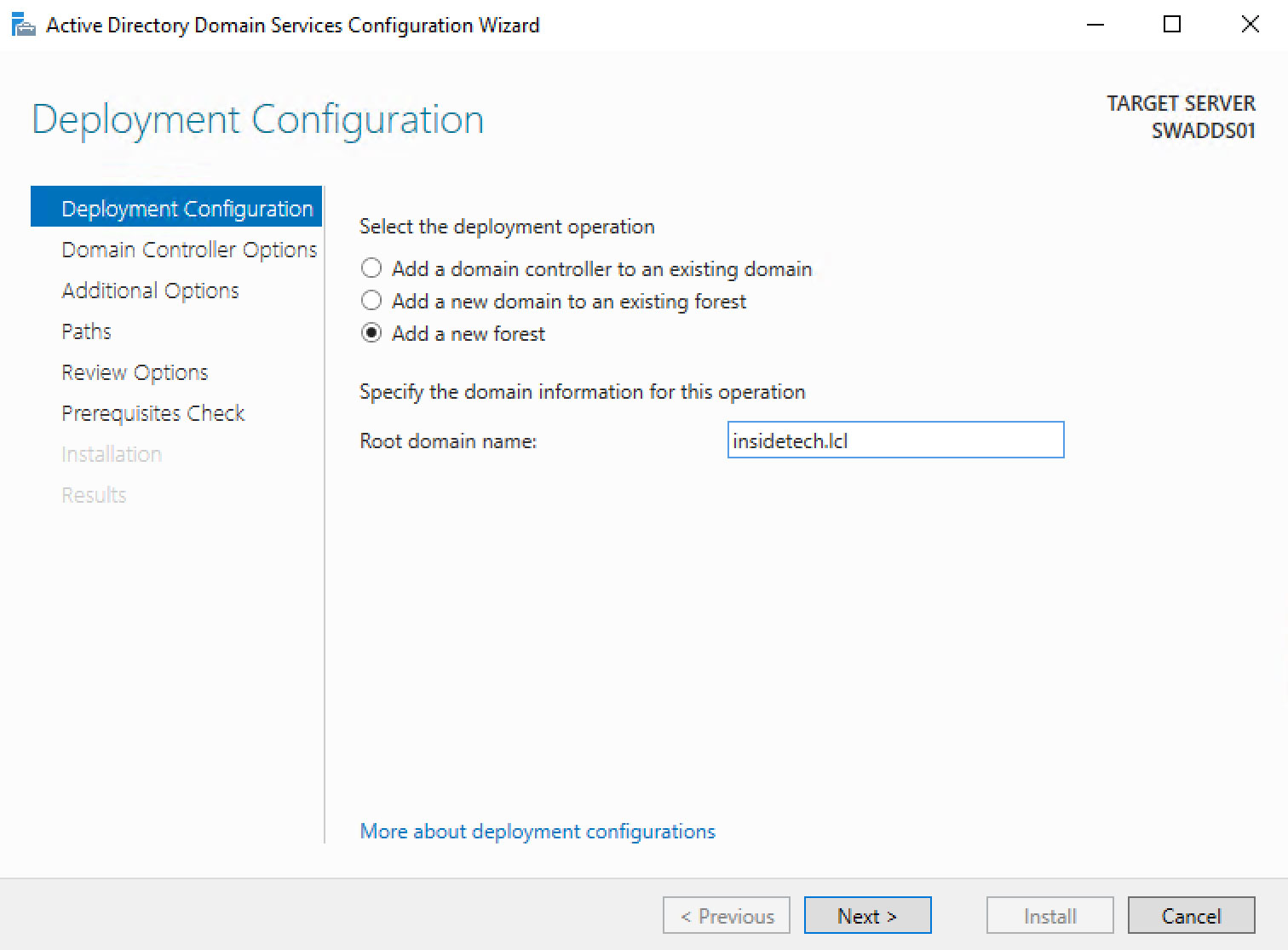
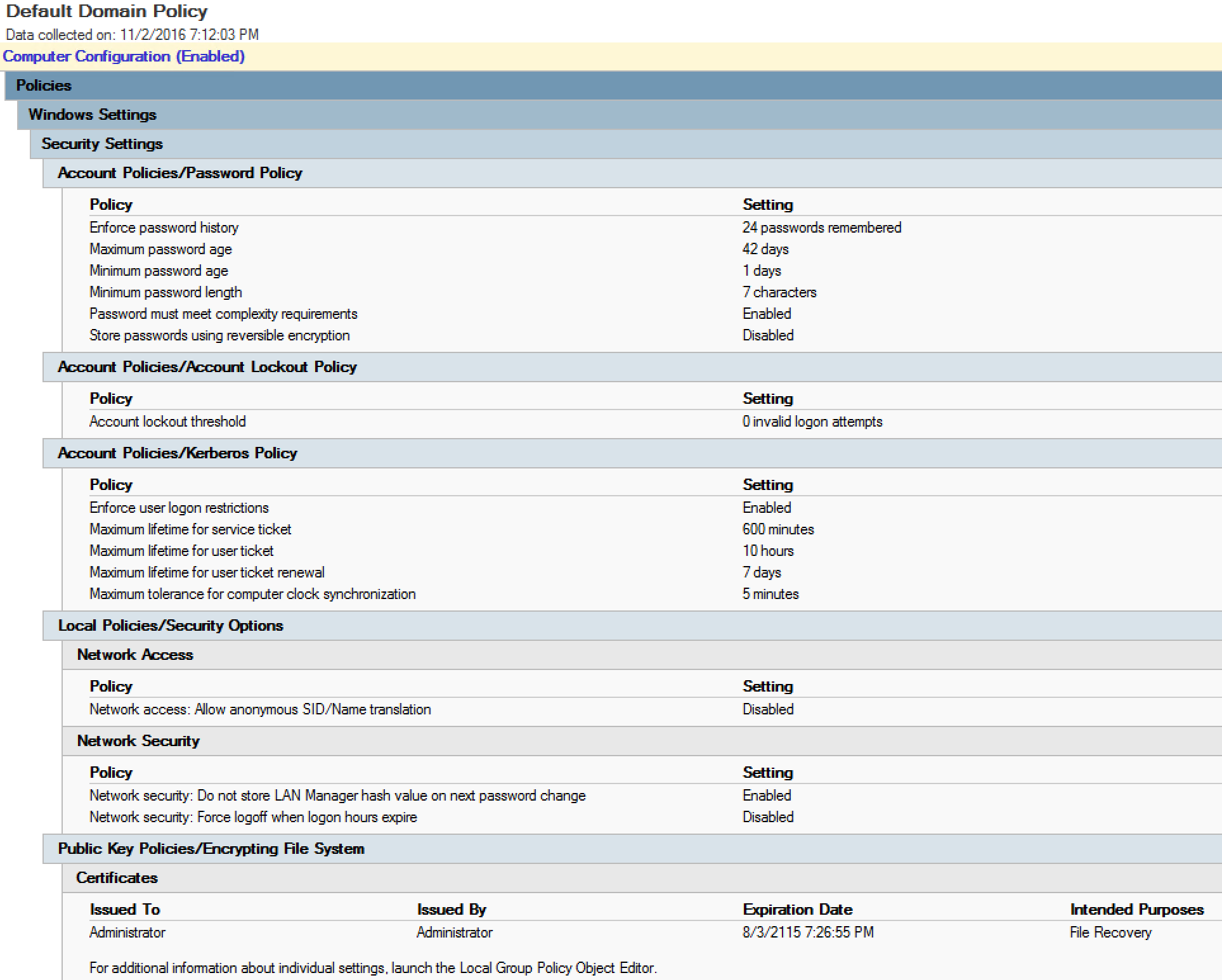
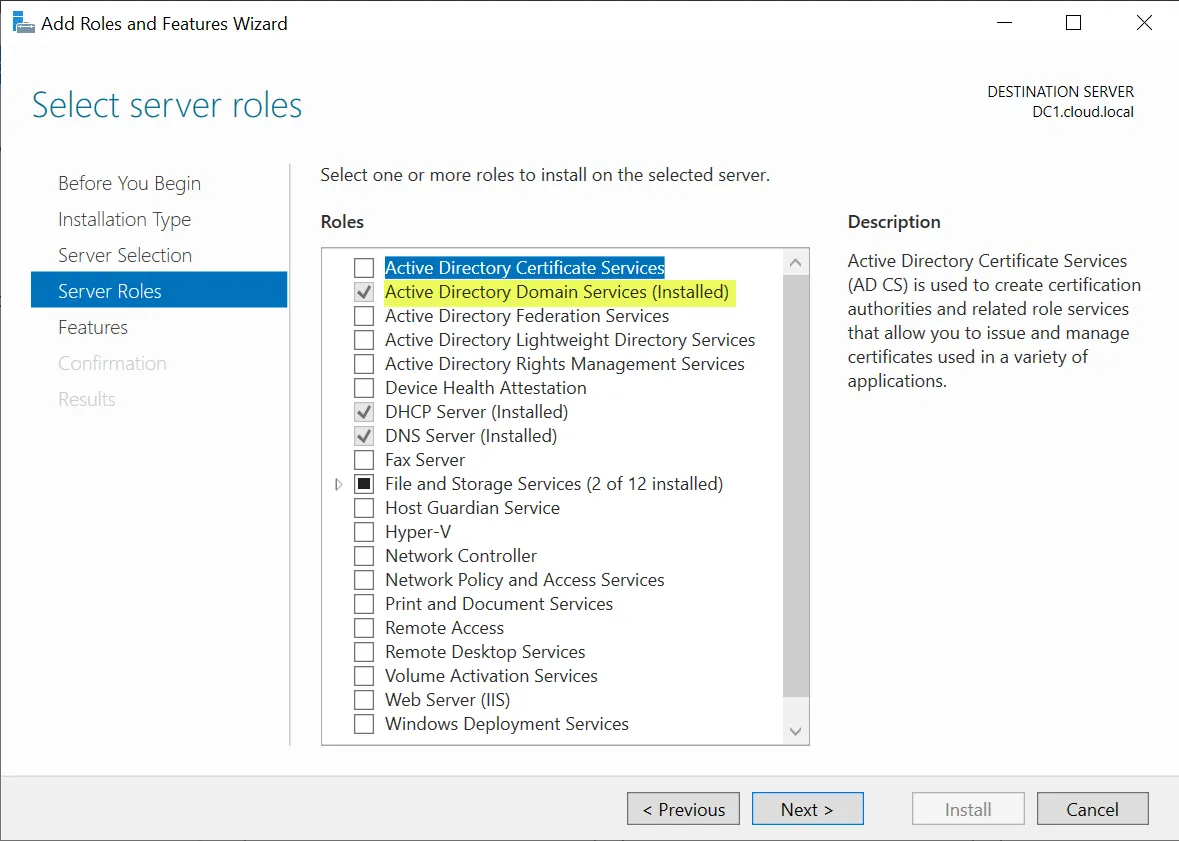
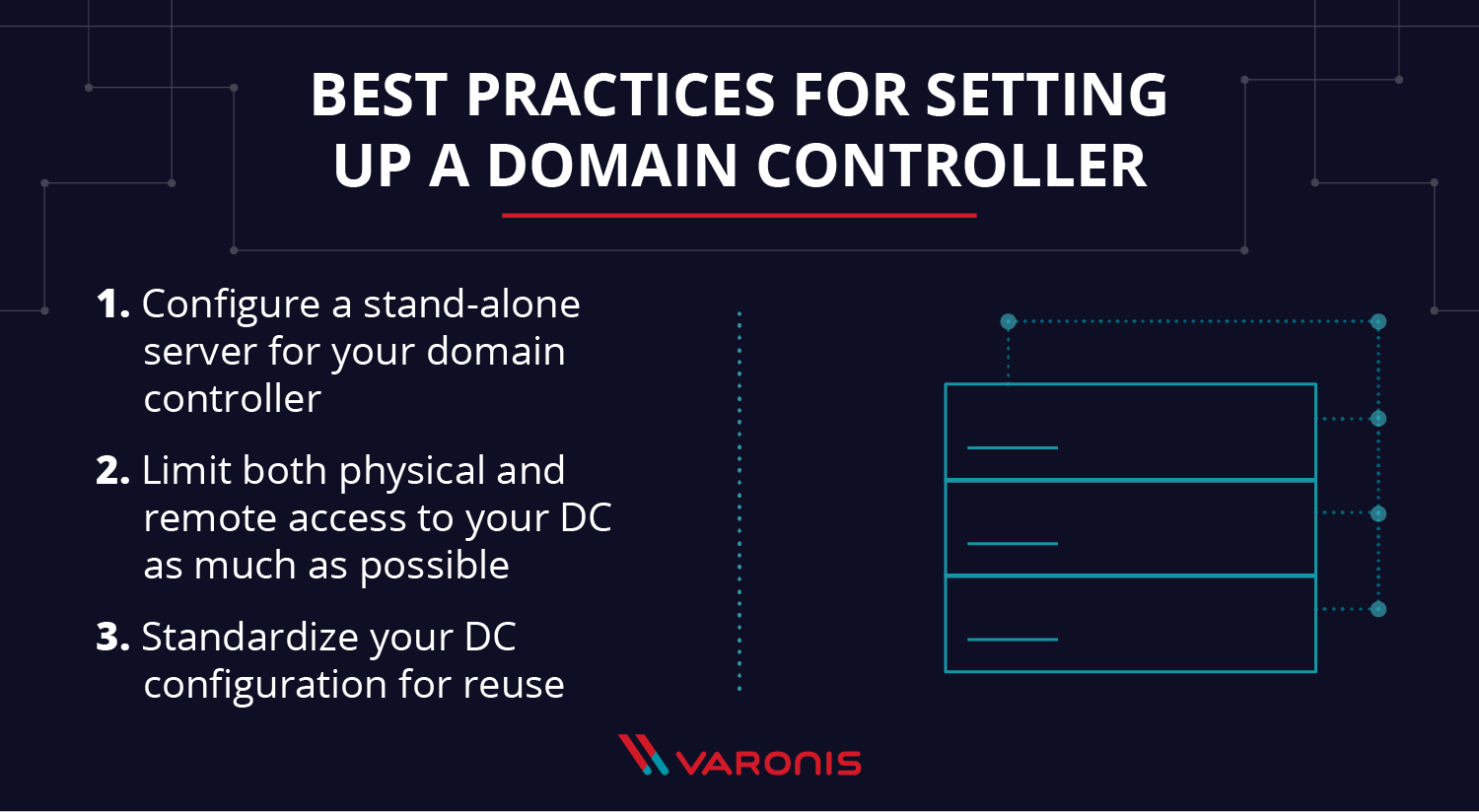
8 Best Practices To Secure Domain Controller - CHARBEL NEMNOM - MVP | MCT | CCSP | CISM - Cloud & CyberSecurity

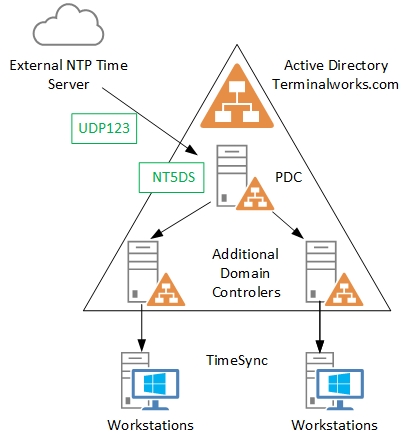
8 Best Practices To Secure Domain Controller - CHARBEL NEMNOM - MVP | MCT | CCSP | CISM - Cloud & CyberSecurity

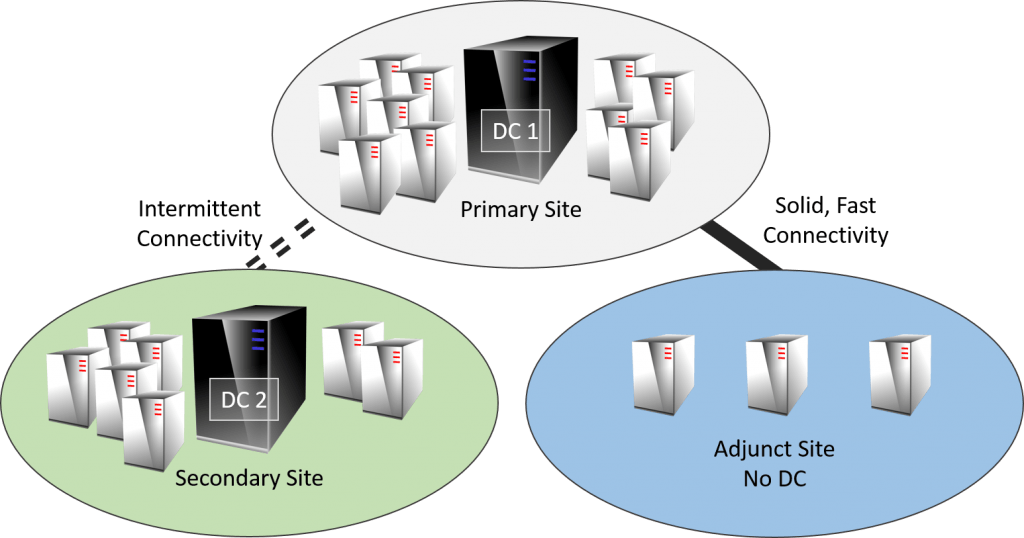
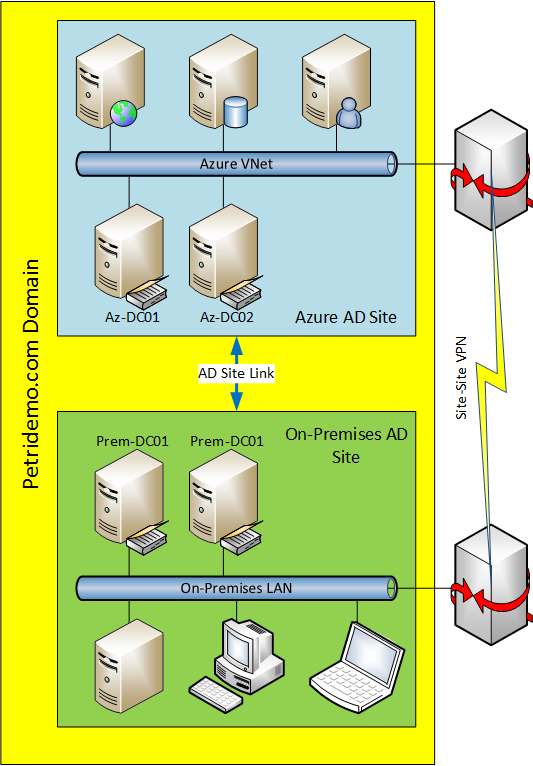
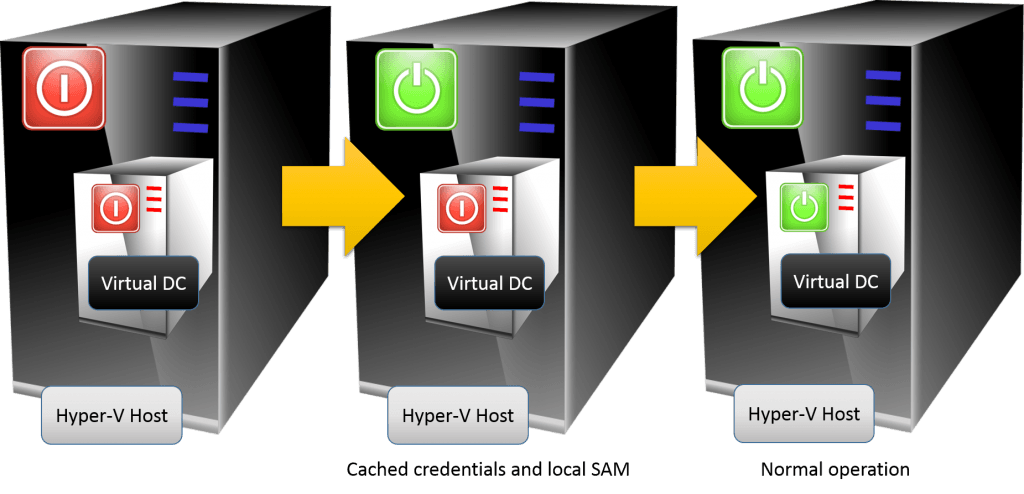
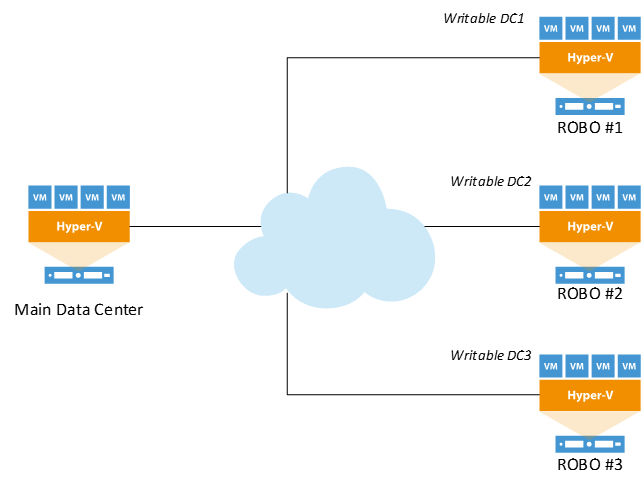
Replication considerations for Domain Controllers running on VMware vSphere - The things that are better left unspoken

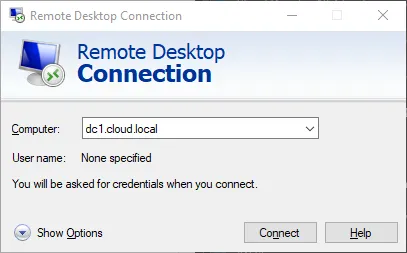
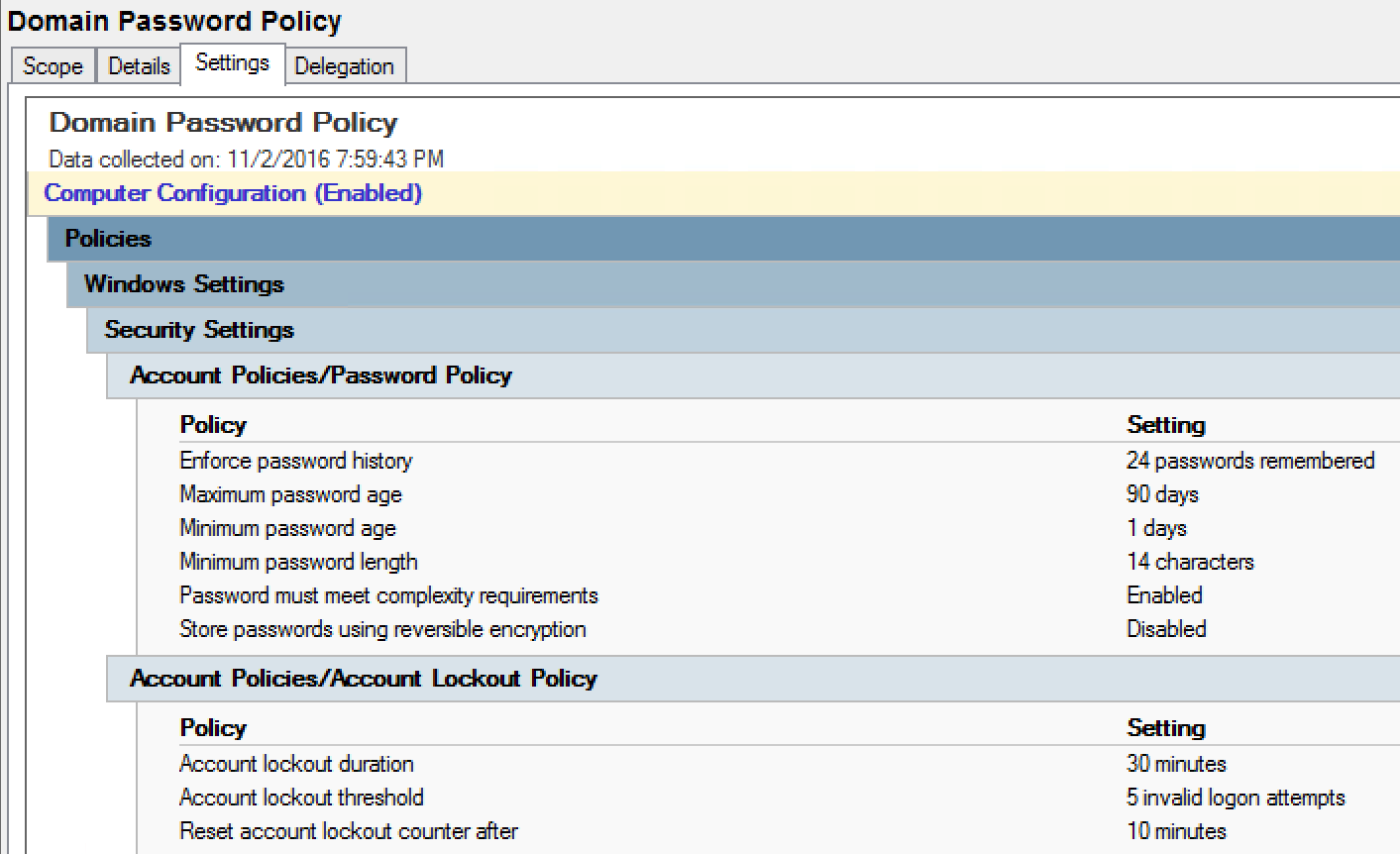
8 Best Practices To Secure Domain Controller - CHARBEL NEMNOM - MVP | MCT | CCSP | CISM - Cloud & CyberSecurity